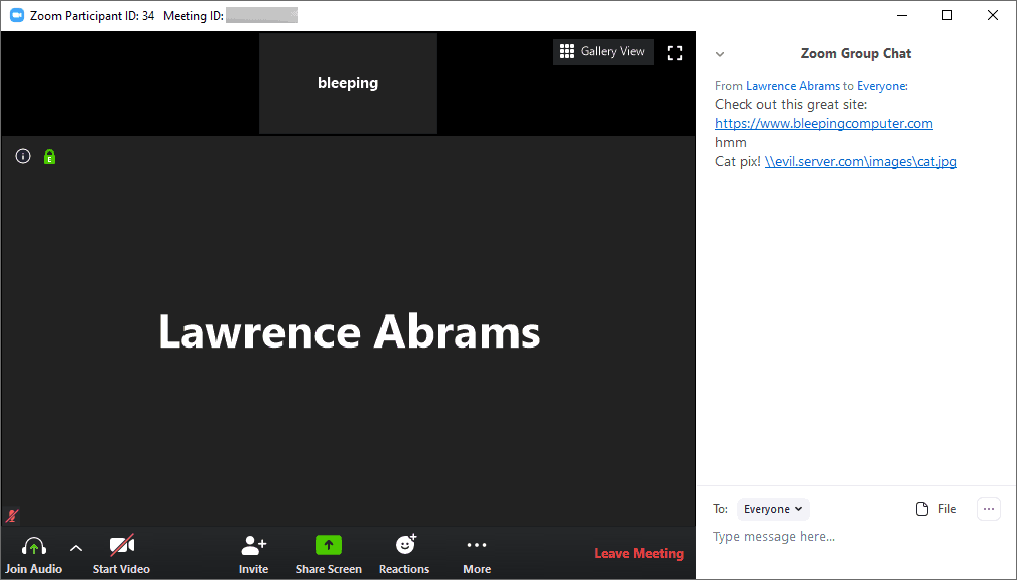
The Conversion Flaw
Zoom’s been having a fine time due to Coronavirus, as the service is used by millions amidst the breakout. Though it’s serving many with their work from home things, it’s deeply scrutinized by many experts for possible flaws. And here it is, blamed for sharing users’ personal data with third-party services like Facebook and now, for a simple flaw which is automatic. Zoom conferencing has a feature that automatically turns any URL into a clickable link so that participants can click on it and open in their default browser. Turns out, it’s also converting UNC paths too into clickable links. Universal Naming Convention (UNC) is a protocol that defines/directs to a resource location. If cleverly mended, it may be tuned as a photo/file storage path. This can be leveraged by attackers to send such malicious links in a group chat, which possibly lets others click on it.
What’s the deal?
UNC protocol is destined to serve the sender with information of about network credentials, by whom the UNC links were clicked. So when a participant clicks on the UNC link, their Windows computer will connect to the attacker’s remote server via the SMB protocol. This process, by default, sends users to log in username and NTLM password hash to the attacker! And cracking a fair NTLM password hash is easy with adequate resources in hand. A security researcher with Twitter name @_g0dmode found this and confirmed by BleepingComputer too. A remedy for this problem by Zoom removing the conversion feature for UNC paths, or users being aware of clicking links. They should differentiate between familiar links and storage paths. If not, BleepingComputer suggested a manual solution like disabling this conversion feature. This can be done by following commands. Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers Via: BleepingComputer