Research and Disclosure
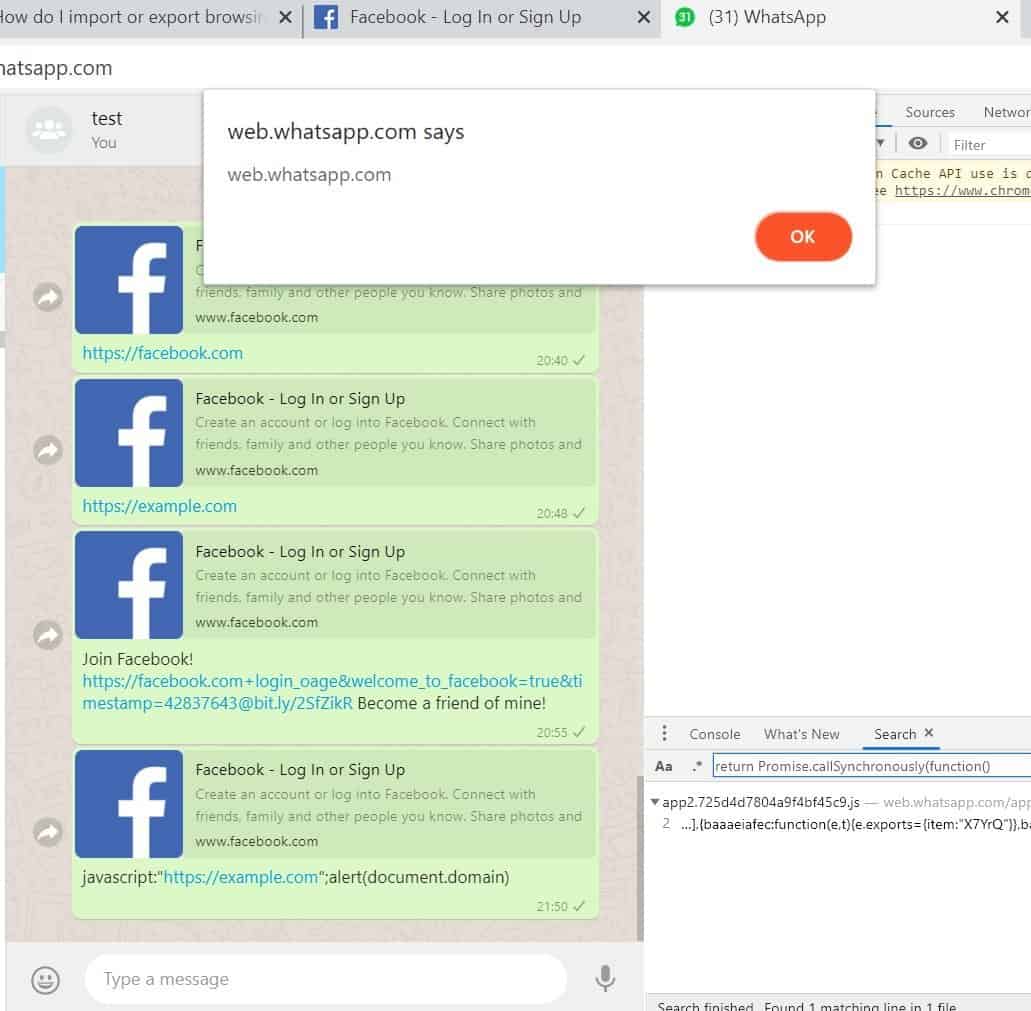
Gal Weizman, a CyberSecurity researcher and a JavaScript expert from Perimeter X, has first found this vulnerability and tested for exploitation. And it worked! The actual flaws were discovered in two major subjects – URL preview and Text message. All he did was modifying the JavaScript code of a text message or a URL preview that’s being sent to the user. The gap he found in WhatsApp’s Content Security Policy if its web version has led him to perform the Cross-Site Scripting (XSS). Here, he managed to pull out the code and look a text message’s JavaScript code and modifying it with any malicious code would eventually lead the user to turn into a victim. But, he needs to do that before the message being delivered to the recipient, which is possible as he tried.
He snooped the code and then crafted a custom code using iframe and let WhatsApp do the general sending thing. While bypassing this CSP being dangerous, this flaw had given him access to the system’s local files too! Imagine an attacker gaining such access and able to send malicious links to users. This flaw can be happening with web URL preview too. So, mind clicking on suspicious links and report messages from spam sources. WhatsApp’s web version v0.3.9309 and below, which are paired with version 2.20.10 are vulnerable for exploitation. Noted as CVE-2019-1842, this vulnerability is rectified by WhatsApp’s parent co., Facebook. A new version of WhatsApp’s web version was released patching this flaw. Eventually, Facebook rewarded Weizman with $12,500 bounty for disclosing it responsibly.