Software Update Serving Malware!
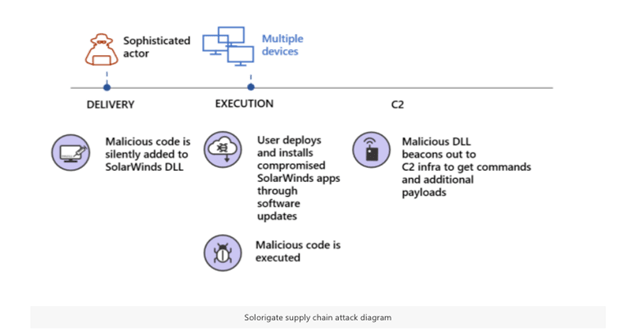
As reported by several publishers and later confirmed by security firms, the US Treasury and the US Department of Commerce’s National Telecommunications and Information Administration (NTIA) were served with a malware-infected software update of Orion, made by SolarWinds. SolarWinds’ Orion is a single-point tool meant to monitor and manage all the devices of a network like the servers, workstations, mobiles, and IoT devices. It’s used by many firms, including the government agencies as above. These were now reportedly inflected with an altered update.
SolarWinds came up with an official statement saying that Orion updates released from March 2020 and June 2020 (v2019.4 to 2020.2.1) were infected with malware. And since it’s pushed to all clients, they may have been infected too by this. It’s also reported that this supply chain attack is how hackers have breached FireEye’s network, a cybersecurity firm, last week. After this, several sources, including The Washington Post and Reuters, have reported Orion software’s compromise. While they linked the threat actors behind this to be APT29, a Russian nation-state backed hacker group, FireEye named it as UNC2452. Soon after this, both FireEye and Microsoft have published notices of the cyberattack with IOCs and measures to counter-attack situations. The malware in question is named SUNBURST (or Solorigate from Microsoft). FireEye added detection rules, and Microsoft did the same to its Defender software. While the number of victims affected by this campaign isn’t disclosed yet, it’s believed that attacks are happening against all types of companies worldwide.