Vulnerable Linux Softwares Exploited With FreakOut Malware
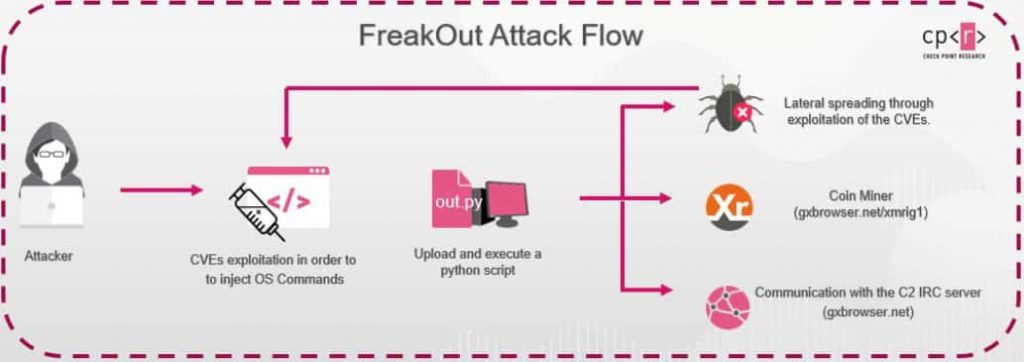
Researchers at Check Point have discovered a new botnet campaign, where the threat actors are abusing the bugs in web applications and NAS device software of Linux. These include the Zend Framework, Liferay Portal, and TerraMaster. Defining more, the TerraMaster is an OS for the NAS devices, where the software’s v4.2.06 and below have an RCE bug that allows remote controlling the device. Zend Framework is a package of professional PHP software having over 570 million downloads. It’s having the same RCE bug in version 3.0.0. And the Liferay Portal, which helps Java developers to build services like custom applications and UI, has a critical bug in v7.2.1, that allows for RCE exploitations. Researchers have pointed out several attacks rising out of these exploitations, from mining cryptocurrencies to spreading throughout the network for reconnaissance.
It starts with the threat actors exploiting any of the above-noted vulnerabilities and injecting a python script, which ultimately the FreakOut malware. It’s said that the malware can perform DDoS attacks, sniffing works like collecting data and scanning ports for the operator. Researchers have also discovered the previous version of the injected python script, that had the comments and authors’ details of the malware. These revealed the malware’s author name to be Freak and IRC based communication channel. Getting the credentials of the latter has even revealed more information on how many devices are being active on the botnet. While there are many to learn about the botnet, researchers said this was active for the last three months, and is growing rapidly. As of now, its task is just to set up an XMRig miner in the victim’s system to mine the Monero cryptocurrency for the operators and could be expanded to others.