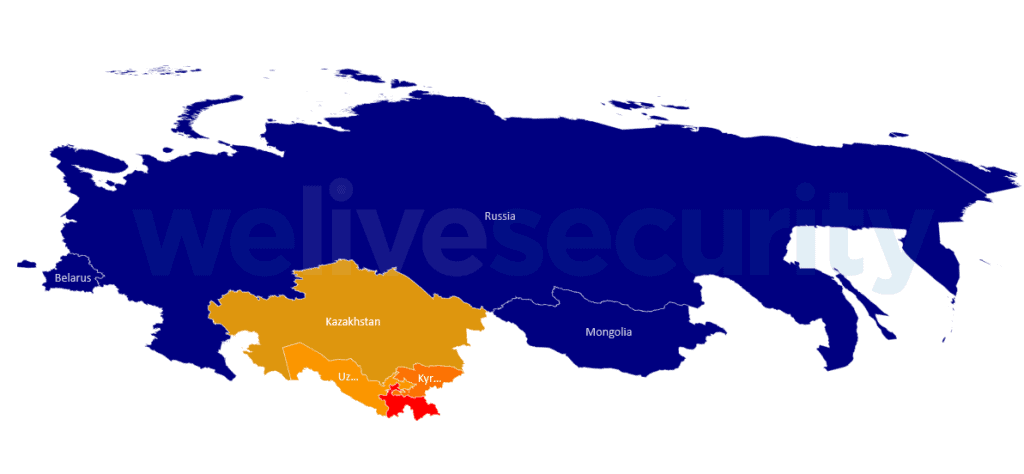
Central Asian Countries as Target
The targets of this RAT are popular telecommunications and gas industries, both private and public companies. Researchers say it’s even existing in a few governments’ networks like Russia, Belarus, and Mongolia. This trojan was first explained by Kaspersky as Microcin in 2017, followed by Palo Alto Networks as BYEBY and by Checkpoint as Vicious Panda. This was now studied in detail by Kaspersky and Avast researchers.
Central Asian Countries as TargetUsing Various Tools To SpreadVia MimikatzVia Windows Management InstrumentThe Gh0st RAT
They admit their inability to know the malware’s tools gained access into the network but explained how it worked after attaining access. Firstly, the attacker with the below code will install a RAT on the target system and tries to crawl laterally throughout the network. This was done using several tools like;
Using Various Tools To Spread
Via Mimikatz
Mimikatz is an open-source tool for bypassing Windows authentication schemes and dump login credentials from memory. While this was developed for red teams as cybersecurity researchers for good cause, it’s often used for exploitations by attackers. Here, it was used to deliver a dropper as installer.exe or Yokel64.exe, which further brings the main payload and an indicative external DLL as mktz64.dll.
Via Windows Management Instrument
Further, attackers used the legitimate Windows tool WMI to spread across the hosting network. Initially, it prepares a remote console to target machine, through the
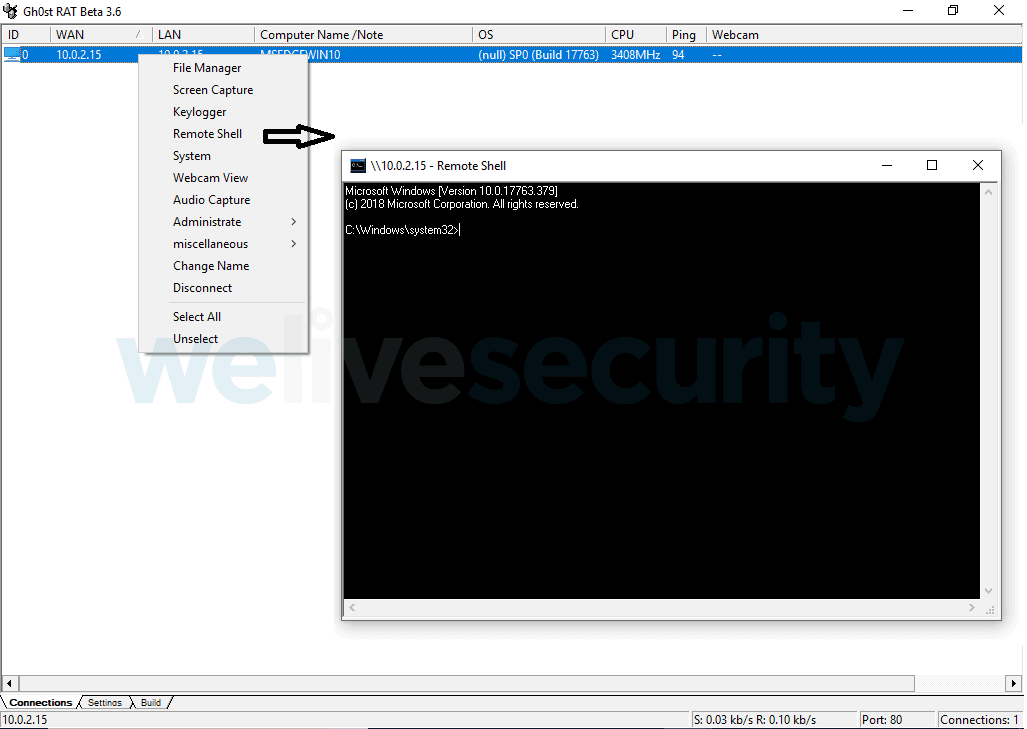
The Gh0st RAT
This trojan is used to connect to a hacker domain, which revealed much about this hack. This RAT will be found as rastls.dll in compromised PC and tries to connect to https://yuemt.zzux[.]com:443 domain. It’s IP address was resolved to locate the server somewhere in China, but still, it’s a kind of proxy. Researchers have even found the server-side client, where the UI seemed too old. But hackers, in this case, using SSL connections, using a variety of tools including the legitimates as from Windows and several layers of obfuscation are appreciated for hiding better. While they’re actively targeting companies and governments in Central Asia, researchers are yet to find out how exactly they’re gaining a foothold into targeted machines in the first place.