JhoneRAT, as described by the discoverer Cisco’s Talos Intelligence Group, is just another data stealer through its infectious malware. Though the goal seemed common, it’s infection workflow is typical. The creators of this have used non-open source code to develop the dropper and Python for RAT malware. And the execution of dumping malware by cloud means and evading flagging creatively, made it stand out.
Common Goal With Typical Execution
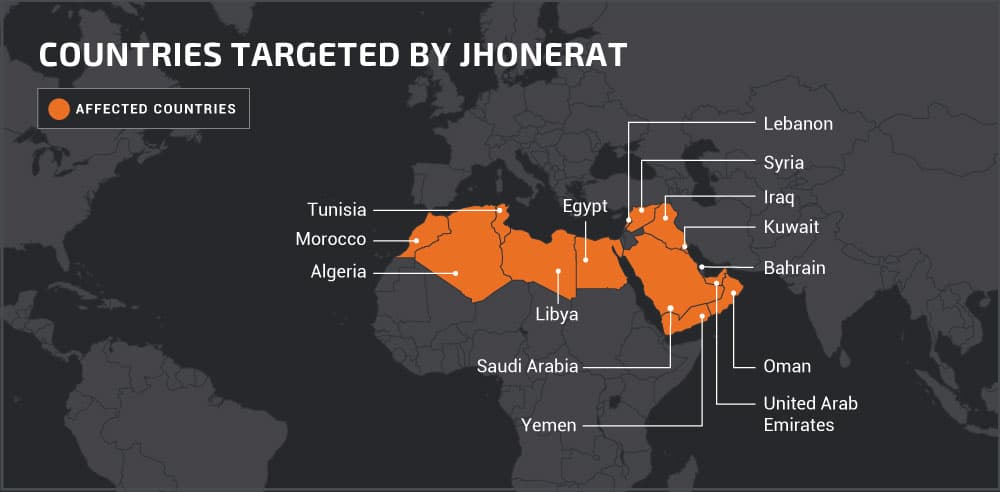
The attacker first chooses the targets, potentially the users from Arabic-speaking nations for unknown reasons through their keyboard layouts and send them Microsoft documents which are hosted in Google Drive. This makes them look legitimate as Google’s Cloud communication is obviously is encrypted by default, which makes Antivirus softwares ignore flagging, and moreover, no detection of suspicious links. Upon opening the document, the attacker urges the victim to open the initial document Urgent.docx, which further prompts the victim to Enable Editing to see an intentionally blurred document. While this being the first level of deceiving, next document as fb.docx contains emails and passwords of a few leaked accounts in 2019! Next document from Drive contains a Macro, which allows an attacker to execute a WMIC command to know the serial number of the victim’s disks, and if it’s unavailable, the code doesn’t execute further. This is to check about the VM detection and download an image from Drive again. The image is of some cartoon’s and its file name is chosen randomly from its dictionary. The image of base64 encoded binary, which leads to the ultimate download of malware RAT that can execute commands from the attacker and send back data in Google Forms. This evades detection by making up all its process in cloud and legitimately looking documents. And finally, the targeted nations are of Saudi Arabia, Iraq, Egypt, Libya, Algeria, Morocco, Tunisia, Oman, Yemen, Syria, UAE, Kuwait, Bahrain and Lebanon.