Must-Know Privacy Features in Android 11
Stressing more on privacy, Google has embedded the following tools in its Android 11 to give users more power to handle their privacy themselves. These are;
Must-Know Privacy Features in Android 11One-time permissionsAccess to Background LocationResetting Permissions AutomaticallyLimiting Storage Access
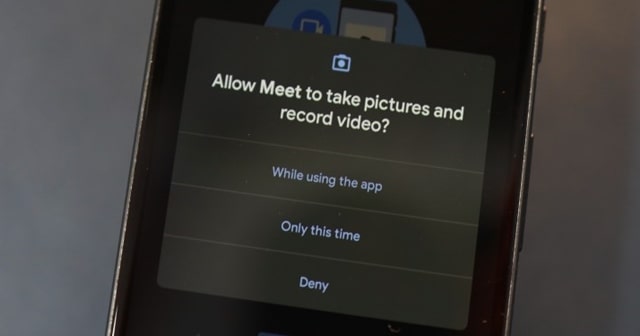
One-time permissions
Users can now allow apps to access their location, camera, or microphone only once or when using the app or deny completely. When opened for the first time, all freshly installed apps will prompt you with a request asking for permission. It’s recommended that users should allow them only if they feel relevant. For example, Google Maps asking for location is relevant, but not for Camera.
Access to Background Location
While users can allow an app to access the location permanently, this has to be set from your phone’s deep settings. This option was removed from the initial prompt request to prevent users from giving away the location access easily and permanently. Thus, apps asking for the location will show only the options While using the app, Only this time, and Deny.
Resetting Permissions Automatically
Users’ permissions to the apps will remain for a while or ask him again when set for one-time but will also be deleted if the user doesn’t use the app for months. This option is available in the Android 11 settings and lets users set for auto-reset of all the permissions given an unused app after a specified time.
Limiting Storage Access
By far, this support seems the most important one of all, as it limits any cyber intrusion. Until now, any app given storage access will be let to check on all the folders in the device’s internal storage. This seems unusual in most cases, as some apps only need access to their own app data. Thus, with Android 11, users can limit an app’s access to storage only to its specified folder. After all, Google has created Project Mainline to make Android devices safer. All devices running on Android 11 can get security updates directly from Google, via Playstore. This eliminates the risk of waiting for the device OEM to push them, letting the shady apps exploit vulnerabilities meanwhile.