Hacking the code masters
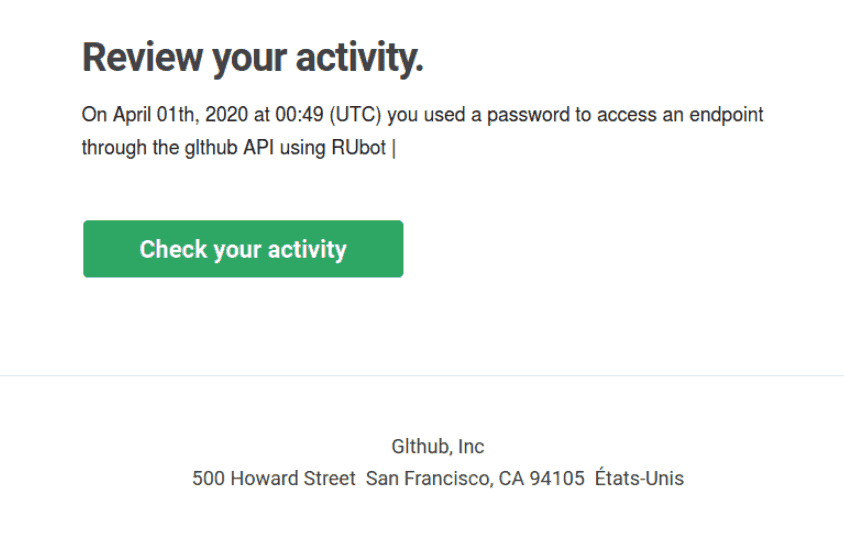
Attackers go after anything that seems lucrative, whether it’s money or knowledge. GitHub reported that an active campaign called Sawfish is targeting towards its users. Many phishing groups were sending unsolicited emails to various users to steal their login credentials and even download their works from private accounts. Most of the targeted users are associated with tech companies and working from distant places. The campaign usually starts with suspicious emails, but the adversaries here are sending emails with legitimate email addresses as notable companies. These were either stolen from previous hacks as compromising email servers or API credentials. They craft the email content in a certain way to invoke a reaction from users like a suspicious activity detected or as a change in settings in their account, thus asking them to review that activity by logging into their account. This would take them to a phishing site and even capture TOTP based two-factor authentication codes along with login credentials. While GitHub said hardware key logins aren’t vulnerable, but once they gain access into anyway, attackers immediately create personal access tokens or authorize OAuth apps for future access, even if the user changes passwords. So GitHub alerted users to be aware of such an email, as they could steal the work and even sell accounts later. It mentioned a few steps like resetting passwords, two-factor recovery codes, reviewing personal access tokens, etc. for safeguard the account. Source: GitHub Blog